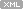The next pattern I would like to talk about is Optimized Code.If you have such cases you should not trust your crash dump analysis tools like WinDbg.Always suspect that compiler generated code might have been optimizedif you see any suspicious or strange behaviour of your tool.Let’s consider this fragmentof stack:
Args to Child
77e44c24 000001ac 00000000 ntdll!KiFastSystemCallRet
000001ac 00000000 00000000 ntdll!NtFsControlFile+0xc
00000034 00000bb8 0013e3f4 kernel32!WaitNamedPipeW+0x2c3
0016fc60 00000000 67c14804 MyModule!PipeCreate+0x48
3rd-party function PipeCreate from MyModule opens a named pipe and its first parameter (0016fc60) points to a pipe name L”\.pipeMyPipe”. Inside the source code it calls Win32 API function WaitNamedPipeW(to wait for the pipe to be available for connection) and passes the same pipe name. Butwe see that the first parameter to WaitNamedPipeW is00000034 which cannot be the pointer to a validUnicode string. And the programshould have been crashedif 00000034 were a pointer value.
Everything becomes clear if we look at WaitNamedPipeWdisassembly (comments are mine):
0:000> uf kernel32!WaitNamedPipeW
mov edi,edi
push ebp
mov ebp,esp
sub esp,50h
push dword ptr [ebp+8] ;Use pipe name
lea eax,[ebp-18h]
push eax
call dword ptr [kernel32!_imp__RtlCreateUnicodeString (77e411c8)]
…
…
…
…
call dword ptr [kernel32!_imp__NtOpenFile (77e41014)]
cmp dword ptr [ebp-4],edi
mov esi,eax
jne kernel32!WaitNamedPipeW+0×1d5 (77e93316)
cmp esi,edi
jl kernel32!WaitNamedPipeW+0×1ef (77e93331)
movzx eax,word ptr [ebp-10h]
mov ecx,dword ptr fs:[18h]
add eax,0Eh
push eax
push dword ptr [kernel32!BaseDllTag (77ecd14c)]
mov dword ptr [ebp+8],eax; reuse parameter slot
As we know [ebp+8] is the first function parameter in non-FPO calls:
Parameters and Local Variables
And we see it is reused because after we convert LPWSTR to UNICODE_STRING and call NtOpenFile to get a handle we no longer need our parameter slot andthe compilercan reuse it to store other information.
Thereisanother compiler optimization we should be aware of and it is called OMAP.Itmovesthe code inside the code sectionand puts the most frequently accessed code fragments together. In that case if you type in WinDbg, for example,
0:000> uf nt!someFunction
you get different code than if you type (assuming f4794100 is the address of the function you obtained from stack or disassembly)
0:000> uf f4794100
In conclusionthe advise is to be alert and conscious during crash dump analysis and inspect any inconsistencies closer.
Happy debugging!
- Dmitry Vostokov -
'Crash dump 불펌스페샬' 카테고리의 다른 글
| Crash Dump Analysis Patterns (Part 7) (2) | 2007.05.13 |
|---|---|
| Crash Dump Analysis Patterns (Part 4) (0) | 2007.05.13 |
| Crash Dump Analysis Patterns (Part 3) (2) | 2007.05.13 |
| Crash Dump Analysis Patterns (Part 2) (1) | 2007.05.13 |
| Crash Dump Analysis Patterns (Part 1) (0) | 2007.05.13 |