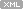Duringkernel debugging training I’mprovidingI came up to the idea to use UML sequence diagrams to depict various Windows kernel behavior including bugchecks.Today I start with bugcheck A. To understand why this bugcheck is needed you need to understand the difference between thread scheduling and IRQL and I use the following diagram to illustrate it:
Then I explain interrupt masking:
Next I explain thread scheduling (thread dispatcher):
And finally here is the diagram showing whenbugcheck Ahappens and what would happenifit doesn’t exist:
This bugcheckhappens in the trap handler and IRQL checking before bugcheck happens in memory manager as you can see from the dump example below. There is no IRQL checking in disassembled handler so it must be in one of Mm functions:
BugCheck A, {3, 1c, 1, 8042d8f9}
0: kd> k
nt!KiTrap0E+0×210
driver!foo+0×209
0: kd> u nt!KiTrap0E nt!KiTrap0E+0×210
nt!KiTrap0E:
…
8046b05e call nt!MmAccessFault (8044bfba)
…
8046b189 call dword ptr [nt!_imp__KeGetCurrentIrql (8040063c)]
8046b18f lock inc dword ptr [nt!KiHardwareTrigger (80470cc0)]
8046b196 mov ecx,[ebp+0×64]
8046b199 and ecx,0×2
8046b19c shr ecx,1
8046b19e mov esi,[ebp+0×68]
8046b1a1 push esi
8046b1a2 push ecx
8046b1a3 push eax
8046b1a4 push edi
8046b1a5 push 0xa
8046b1a7 call nt!KeBugCheckEx (8042c1e2)
- Dmitry Vostokov -
'Crash dump 불펌스페샬' 카테고리의 다른 글
| Crash Dump Analysis AntiPatterns (Part 4) (0) | 2007.05.14 |
|---|---|
| Crash Dump Analysis AntiPatterns (Part 2) (0) | 2007.05.14 |
| Crash Dump Analysis AntiPatterns (Part 3) (0) | 2007.05.14 |
| Crash Dump Analysis AntiPatterns (Part 1) (0) | 2007.05.14 |
| Crash Dump Analysis Patterns (Part 13a) (1) | 2007.05.14 |